Ensuring Accountability: Metadata & Audit Trails in Digital Evidence
by Daniyal Hassan, Last updated: February 17, 2026, ref:

Digital evidence is no longer supplementary. In modern investigations, it is often central to decision-making. Surveillance recordings, mobile device extractions, cloud logs, internal communications, and transactional records increasingly determine investigative outcomes across law enforcement, regulatory agencies, and corporate environments.
As reliance on digital artifacts grows, so does exposure. Unlike physical evidence, digital files can be duplicated, altered, or transferred without visible indicators. A file may appear intact while its history remains unclear. When organizations cannot demonstrate how evidence was handled, confidence shifts from certainty to doubt.
In environments where cases may face legal scrutiny, regulatory review, or public transparency requirements, doubt is costly. Accountability mechanisms exist to prevent that erosion of trust.
Where Accountability Breaks Down
Accountability failures rarely result from deliberate misconduct. More often, they develop gradually through fragmented processes and routine operational decisions. A file may be shared without documentation, permissions adjusted without oversight, or system changes made without preserving contextual data. Individually, these actions seem minor. Over time, they create uncertainty.
That uncertainty surfaces when evidence is challenged. The focus shifts from what the evidence shows to how it was handled. If access history, transfers, or system changes cannot be clearly demonstrated through structured records, the organization must rely on explanation rather than verification. In high-stakes environments, that distinction can determine credibility.
Structured accountability mechanisms reduce this risk by embedding transparency into everyday evidence handling before gaps become liabilities.
How Lack of Accountability Compromises Digital Evidence
Weak accountability rarely causes immediate collapse. It creates gradual exposure.
When organizations cannot clearly demonstrate how evidence was accessed, transferred, or preserved, three risks emerge:
1. Legal Vulnerability
If handling cannot be verified, authenticity may be questioned. Even unchanged evidence can lose credibility when its history is unclear.
2. Security Exposure
Without reliable activity records, unauthorized access or misuse becomes difficult to trace, limiting the ability to contain incidents or prove integrity after the fact.
3. Operational and Compliance Strain
Audits and reviews become slower and more complex when teams must reconstruct evidence history manually. As data volumes increase, these inefficiencies scale.
Accountability gaps do not always appear during routine operations. They surface under scrutiny.
Bringing Metadata and Audit Trails Together
Metadata and audit trails address different dimensions of accountability, but their value emerges when they operate in alignment.
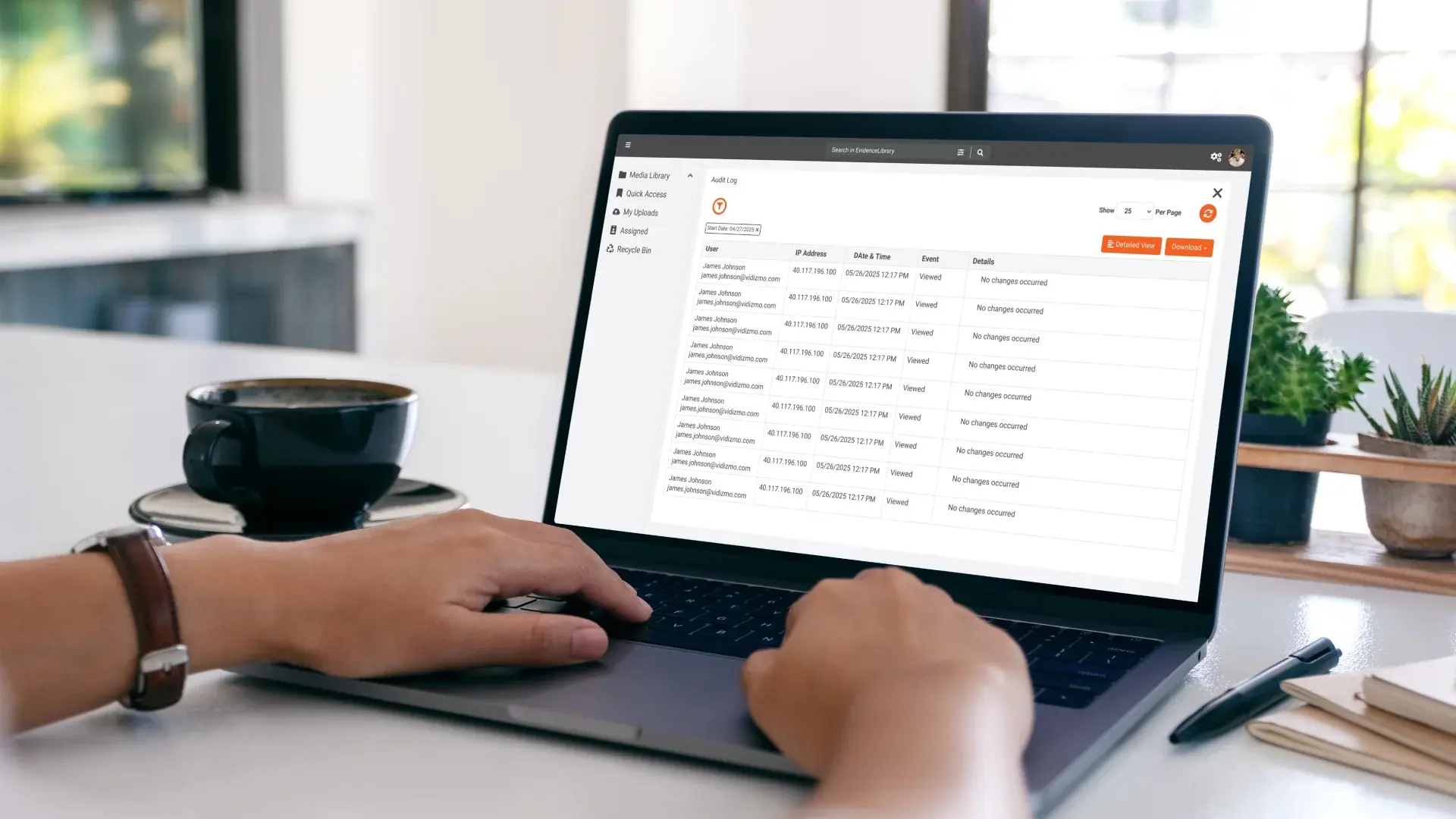
Metadata establishes context. It preserves the attributes that explain where evidence originated and how it evolved. Audit trails establish stewardship. They document how that evidence was handled after collection. When both are preserved consistently, organizations gain visibility across the entire lifecycle of digital evidence.
See our guide on Metadata and Audit Integrity in Digital Evidence Management for more detail.
This lifecycle visibility is what transforms isolated technical controls into institutional accountability. Context without traceability leaves handling unclear. Traceability without preserved context leaves authenticity open to question. Together, they create continuity.
In high-stakes environments, continuity is not optional. It enables organizations to demonstrate that evidence remained intact, was accessed appropriately, and was managed according to defined procedures. That demonstration protects credibility long before a challenge arises.
Why Accountability Must Be Embedded in Evidence Governance
Accountability in digital evidence management cannot depend on informal practice or individual diligence. As digital artifacts become central to investigations, oversight must be structured and consistently enforced.
Embedding accountability into evidence governance requires three foundational commitments:
1. Clear Policies
Documented procedures must define how evidence is collected, accessed, transferred, and retained.
2. Defined Responsibility
Roles and permissions should be explicitly assigned so accountability is traceable, not assumed.
3. Continuous Oversight
Controls such as contextual preservation and activity logging must be maintained and periodically reviewed to ensure they remain effective as systems and personnel evolve.
When these elements are embedded into everyday operations, procedural gaps are less likely to emerge. In high-stakes environments, credibility is not assumed. It is sustained through disciplined governance.
Responsibility Across Collection, Access, and Oversight
Accountability in digital evidence management must extend across the entire evidence lifecycle. It begins at collection, where contextual information should be preserved and evidence entered into controlled systems without informal handling. Gaps introduced at this early stage rarely disappear; they compound over time.
As evidence moves into review and analysis, responsibility shifts but does not diminish. Access permissions must align with defined roles, and interactions must remain traceable so that handling can be demonstrated rather than assumed. Even routine actions, when undocumented, create ambiguity that weakens stewardship.
Oversight completes the lifecycle. Supervisors and compliance functions must periodically review how evidence is managed to ensure that policies remain effective as systems evolve and operational demands increase. Without structured oversight, small deviations can mature into systemic weaknesses.
When responsibility is continuous rather than segmented, accountability becomes embedded in practice, reinforcing institutional credibility at every stage.
Organizations that manage high volumes of digital evidence should periodically assess whether their systems and governance structures provide demonstrable accountability across the evidence lifecycle.
Key Takeaways
- Digital evidence now plays a central role in investigations across law enforcement, regulatory, and corporate environments.
- Unlike physical evidence, digital files can be altered or mishandled without visible indicators, increasing governance risk.
- Accountability gaps often emerge gradually through fragmented processes rather than deliberate misconduct.
- Weak oversight can lead to legal vulnerability, security exposure, and operational inefficiency.
- Metadata preserves contextual transparency, while audit trails provide procedural traceability.
- When aligned across the evidence lifecycle, these mechanisms strengthen institutional credibility.
- Accountability must be embedded into evidence governance through clear policies, defined responsibilities, and ongoing oversight.
People Also Ask
Accountability ensures that digital evidence remains trustworthy. Without structured documentation of how evidence was handled, organizations face increased legal, security, and compliance risks.
Credibility can be weakened when access history, transfers, or system changes cannot be clearly demonstrated. Even unchanged evidence may be questioned if its handling lacks traceability.
Metadata preserves contextual information about the origin and history of digital evidence, helping organizations maintain transparency and reconstruct timelines.
Audit trails document interactions with evidence over time, providing visibility into access and handling activities. This traceability reduces ambiguity during legal or regulatory review.
Responsibility spans the entire evidence lifecycle, including investigators, administrators, compliance teams, and leadership. Effective accountability requires coordinated governance across these roles.
Jump to
You May Also Like
These Related Stories
Importance of Metadata and Audit Trails in Digital Evidence Management

Chain of Custody for Digital Evidence: Importance, Best Practices, and How to Maintain It


No Comments Yet
Let us know what you think