Importance of Metadata and Audit Trails in Digital Evidence Management
by VIDIZMO Team, Last updated: February 17, 2026, ref:
Two decades ago, digital evidence played a limited role in investigations. Today, it is central to nearly every criminal, regulatory, and internal inquiry. From body worn camera footage and surveillance video to emails, text messages, and cloud records, the volume and variety of digital data have expanded dramatically.
The National Institute of Justice defines digital evidence as information stored or transmitted in binary form that may be relied upon in court. Its relevance alone is not enough. For digital evidence to be admissible and credible, its integrity must be preserved and demonstrable.
.webp?width=500&height=300&name=featureimage%20(2).webp)
As data volumes grow, preserving evidence integrity becomes more complex. Storage alone is not enough. Organizations need structured systems that centralize evidence, control access, document activity, and maintain chain of custody.
Digital Evidence Management Systems provide this framework. Two controls are central to that framework: metadata preservation and audit logging. Metadata establishes origin and characteristics, while audit trails document how evidence is accessed and handled over time. Together, they support authenticity, accountability, and continuity.
This article examines how these controls strengthen defensible evidence management.
What is Metadata?
Metadata is structured information that describes the origin, characteristics, and history of a digital file.
In a digital evidence context, metadata provides context that the visible content cannot. It may indicate when a file was created, which device captured it, who modified it, or whether it has changed since collection. In many cases, metadata becomes central to reconstructing timelines or validating authenticity. For a broader overview of how metadata and audit mechanisms establish accountability in investigations, see our guide on ensuring accountability in digital evidence.
Unlike ordinary file storage environments, digital evidence systems must preserve metadata exactly as captured. If metadata is altered, overwritten, or inconsistently retained, evidentiary reliability may be compromised.
This is why metadata in digital evidence management is not simply descriptive. It is foundational to credibility.
What Are the Types of Metadata You Should Know About?
In digital investigations, metadata generally falls into four categories, each supporting authenticity and context in different ways.
1. File System Metadata
Creation dates, modification timestamps, file size, and ownership details. Often used to reconstruct timelines and validate sequence of events.
2. Embedded Metadata
Data stored within the file itself, such as EXIF information in images or GPS coordinates in video. Helps confirm capture time, device, and sometimes location.
3. Application Metadata
Information generated by the software used to create or edit a file, including authorship fields and revision history. Relevant in authorship or modification disputes.
4. System Generated Metadata
Metadata created by the evidence management system during ingestion and storage, such as upload timestamps and cryptographic hash values used to verify integrity.
Together, these categories establish origin, chronology, and continuity, which are essential in digital evidence management.
Can Metadata Be Used as Evidence?
Yes. Metadata can serve as evidence when it establishes authenticity, timeline, or integrity.
Courts and regulatory bodies increasingly treat metadata as probative, particularly when it clarifies authorship, sequence of events, or confirms that a file has not been altered. However, admissibility depends on reliability. If metadata can be modified without detection, or if its preservation cannot be demonstrated, its evidentiary value weakens.
To withstand scrutiny, metadata must be preserved in its native form, protected against unauthorized alteration, linked to documented chain of custody, and supported by reliable audit logging.
Metadata alone is rarely sufficient. Its strength ultimately depends on the integrity of the system that stores and tracks it, which is where audit trails become essential.
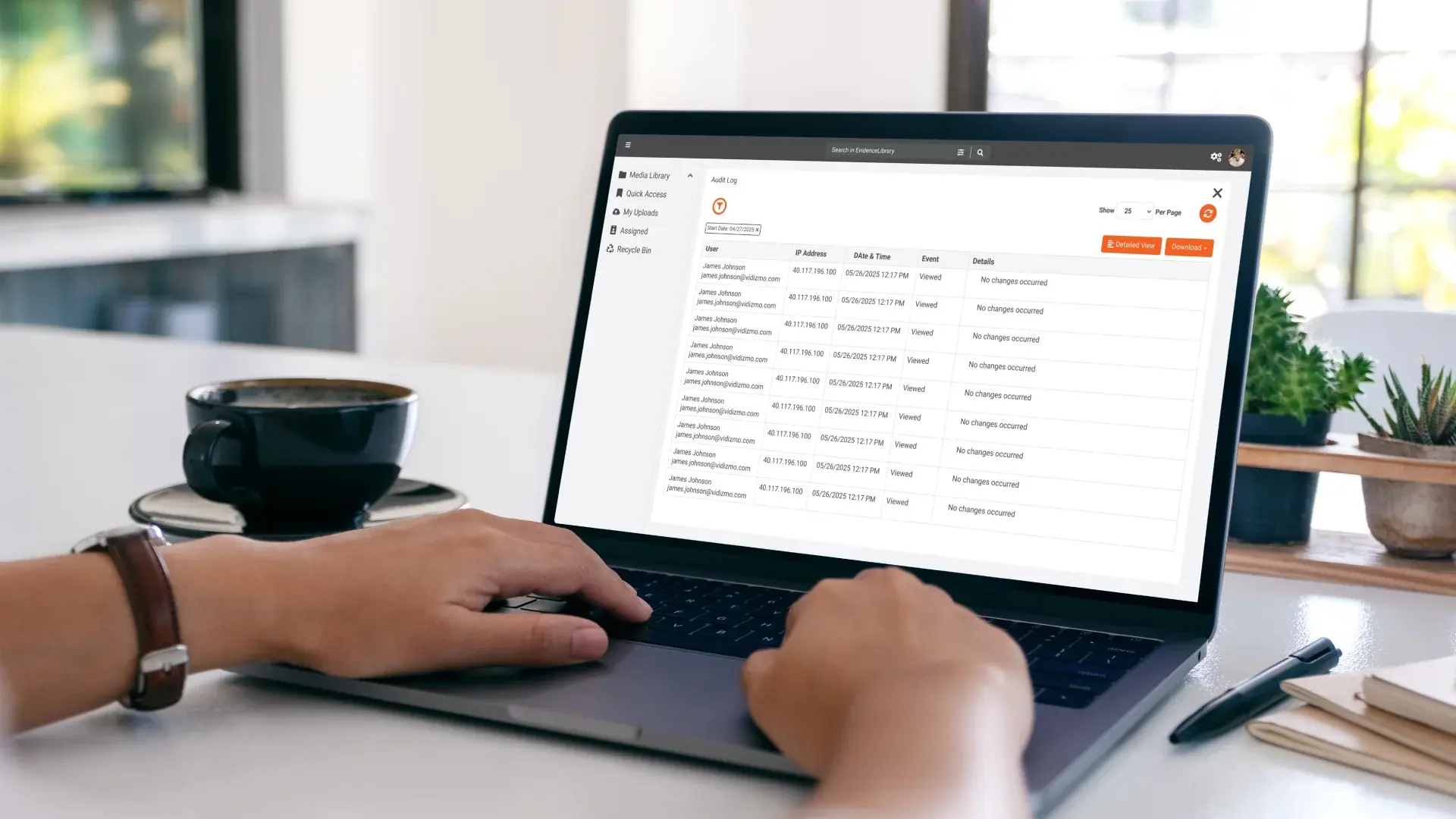
What Are Audit Trails in Digital Evidence Management Systems?
An audit trail is a chronological record of activity within the evidence management environment.
It documents how digital evidence is accessed, handled, shared, exported, or administratively modified. In practical terms, it creates an accountability record for every interaction with evidence.
When evidence is reviewed in court or by regulators, the focus often shifts to process. Who accessed the file. Was it altered. Was it exported outside authorized controls. Were permissions enforced consistently.
A well structured audit trail answers these questions with clarity and documentation.
What Does an Audit Trail Consist of in Digital Evidence Management Systems?
In a defensible digital evidence environment, an audit trail should capture more than simple access logs. It must document the full lifecycle of evidence handling in a way that supports integrity and accountability.
A comprehensive audit trail typically includes:
1. User Attribution
Every action must be tied to an authenticated user identity. Anonymous or shared account activity weakens accountability.
2. Timestamp Integrity
All events should be recorded using synchronized system clocks to prevent disputes over chronology.
3. Activity Logging
The system should record viewing, editing, exporting, sharing, deletion attempts, and administrative configuration changes. Both successful and failed access attempts should be captured.
4. Administrative Oversight Logging
Changes to permissions, roles, retention policies, and system settings must be logged to prevent unnoticed privilege escalation.
5. Integrity Protection of Logs
Audit records themselves should be protected against tampering. In mature systems, logs are immutable or cryptographically secured.
6. Hash Verification Support
Cryptographic hash values generated at ingestion create a digital fingerprint. Revalidation of that fingerprint confirms that evidence has not changed over time.
Compliance frameworks such as CJIS, HIPAA, NIST 800 53, and ISO 27001 reinforce these expectations. In regulated environments, audit depth is not optional. It directly influences evidentiary defensibility.
Organizations handling legally sensitive digital evidence should periodically evaluate whether their audit trail architecture meets both operational and compliance driven requirements before external scrutiny exposes gaps.
Do Metadata and Audit Trails Work Together?
Metadata and audit trails perform different roles, but evidentiary defensibility depends on their alignment.
They work together in the following ways:
1. Authenticity and Accountability
Metadata establishes origin, creation details, and file characteristics. Audit trails document who accessed or handled the file after collection. One confirms what the file is, the other confirms how it was managed.
2. Timeline Validation
Metadata may indicate when a file was created or captured. Audit logs then validate subsequent events such as review, transfer, or export. Together, they create a defensible chronology.
3. Chain of Custody Continuity
Metadata supports initial authenticity, while audit trails document every step in the custody process. If either is incomplete, continuity becomes vulnerable to challenge.
4. Integrity Verification
System generated metadata such as cryptographic hash values can confirm that a file remains unchanged. Audit trails show whether any action occurred that could affect that integrity.
When both elements are preserved and protected, digital evidence demonstrates authenticity, traceability, and procedural control. If one is weak, the credibility of the entire record may be questioned.
Evaluating Metadata and Audit Integrity in Digital Evidence Management
Digital evidence management systems vary significantly in how they preserve metadata and enforce audit controls. Superficial feature comparisons often overlook structural differences that affect evidentiary defensibility.
When evaluating a platform, focus on four core areas:
1. Metadata Preservation
The system should retain native metadata at ingestion and generate system level metadata to support classification and lifecycle management.
2. Integrity Verification
Cryptographic hashing should be applied upon upload, with the ability to revalidate file integrity during review or export.
3. Audit Depth and Protection
Granular logging must capture user activity, exports, administrative changes, and failed access attempts. Audit records should be protected against alteration and retained according to policy.
4. Compliance and Deployment Alignment
Logging architecture should support regulatory expectations and maintain consistent timestamp synchronization across cloud, hybrid, or government environments.
VIDIZMO Digital Evidence Management System incorporates native metadata preservation, cryptographic hashing, detailed audit logging, and role based access controls to support defensible evidence management in regulated environments.
If you have any questions or concerns, please leave a message in the comment section below or reach out to us today!
Key Takeaways
- Digital evidence now plays a role in the vast majority of investigations, increasing the need for structured integrity controls.
- Metadata provides contextual proof of origin, timeline, authorship, and file characteristics.
- The main types of metadata include file system, embedded, application, and system generated metadata.
- Metadata can be used as evidence when it is preserved in its native form and supported by reliable audit logging.
- Digital audit trails document who accessed, modified, exported, or administered evidence throughout its lifecycle.
- A defensible audit trail includes authenticated user attribution, synchronized timestamps, granular activity logging, hash verification, and tamper protection.
- Compliance frameworks such as CJIS, HIPAA, NIST 800 53, and ISO 27001 reinforce the need for traceable and protected logging.
- Metadata and audit trails work together to maintain chain of custody, validate integrity, and support evidentiary credibility.
- When evaluating a Digital Evidence Management System, integrity architecture matters more than surface level features.
People Also Ask
Yes. Metadata can support authenticity, timeline validation, and file integrity when it is preserved within a secure system that maintains reliable audit logs and chain of custody documentation.
The primary types include file system metadata, embedded metadata such as EXIF data, application metadata such as revision history, and system generated metadata including cryptographic hash values.
A digital audit trail is a chronological record of user and system activity related to digital evidence handling, including access, modification attempts, exports, and administrative changes.
A defensible audit trail should include authenticated user attribution, synchronized timestamps, detailed activity logging, administrative oversight tracking, tamper protection, and support for hash based integrity verification.
Metadata establishes the origin and characteristics of evidence, while audit trails document every action taken after collection. Together, they create continuity and accountability throughout the evidence lifecycle.
Jump to
You May Also Like
These Related Stories
.jpg)
Tamper Detection: How it Works to Keep Digital Evidence Safe?

8 Major Challenges in Handling Digital Evidence and How to Solve Them




No Comments Yet
Let us know what you think