Governance and Compliance in Corporate Video Libraries: From Risk Exposure to Trusted System of Record
by Rafay Muneer, Last updated: January 5, 2026, ref:

Your corporate video library likely contains more risk than you think. Not just training clips and town halls. It holds recorded customer calls, product demos with roadmaps on screen, HR investigations, internal incident reviews, board meetings, and regulated communications.
Now imagine this content floating around with open links, no video access control, no audit trails for video, and no clear ownership. You cannot see who watched what, you cannot prove compliance, and you cannot reliably delete anything on time. That is an audit finding waiting to happen.
This is the core governance problem. Video is treated as a side channel, while written content and documents already sit in tightly governed systems. Yet the corporate video library is now a major system of record. It captures evidence of decisions, intent, and behavior. If video governance is weak, your legal, security, and compliance exposure grows with every new upload.
Buyers who own risk know this pain. They see shadow libraries on shared drives, chat tools, and unmanaged cloud folders. They get last minute requests from legal to find a recording from two years ago. They hear security teams complain about open links. They hear employees say they do not trust the corporate video library because they do not know who can see what.
Without clear enterprise video governance, video becomes unsearchable, unprovable, and uncontrollable. In other words, a liability, not an asset.
Common governance risks in unmanaged corporate video libraries
Most issues trace back to the same pattern. Video spreads faster than governance can catch up. Common risks include:
Open links and uncontrolled sharing
Public or unprotected links create major video compliance gaps. Risks include:
- Sensitive videos accessible to anyone who guesses or forwards a link
- Regulated information leaving controlled environments
- No way to revoke access centrally when situations change
From a compliance perspective, open links break the chain of custody. You cannot say with confidence who has seen what, or when.
No granular access control
Many corporate video libraries rely on simple folder-level permissions or manual sharing. That is not sufficient for enterprise video governance. Gaps include:
- Role changes not reflected in video access control
- Former employees or contractors retaining access to sensitive recordings
- Business units creating their own rules that conflict with policy
The result is inconsistent secure video management across teams and regions. It also increases the chance of policy violations and accidental disclosure.
No audit history or immutable logs
When auditors or regulators ask who accessed a specific video, many organizations cannot answer. They lack:
- Comprehensive audit trails for video views, downloads, shares, and changes
- Immutable logs that stand up as legal evidence
- Searchable reports for investigations and eDiscovery
Without this level of visibility, it is difficult to prove compliance, detect misuse, or support internal investigations.
Undefined retention and deletion
Another common gap in a corporate video library is unclear retention. Videos pile up indefinitely. Nobody owns them. Risks include:
- Keeping regulated communications longer than policy allows
- Retaining personal data without a lawful purpose
- Holding discoverable content that should have aged out under record retention rules
Video retention policies are key. Without them, organizations either over-retain and carry risk, or purge content reactively and lose potential evidence and institutional knowledge.
Core governance pillars for secure video management
A governed corporate video library rests on a few non negotiable pillars. These turn ad hoc video storage into an accountable, compliant, and auditable environment.
Role based access control
Access must follow your organizational structure and policies. That means:
- Role based access tied to HR or identity systems
- Group and attribute based rules for sensitive content
- Automatic updates when people join, move, or leave
This level of video access control reduces manual exceptions and keeps entitlements consistent. It also supports segregation of duties, which is central to many compliance frameworks.
Strong authentication and authorization
Secure video management starts with identity. A corporate video library should integrate with your existing stack, including:
- Single sign on and SAML or OpenID Connect
- Multi factor authentication policies
- Conditional access rules by location, device, or risk score
Once users authenticate, authorization enforces who can upload, publish, share, embed, or download. Clear separation of viewer, contributor, and admin roles supports a least privilege model.
Retention and deletion policies
Mature enterprise video governance treats video as a formal class of records. This requires:
- Configurable video retention policies by category, department, or region
- Automatic deletion or archival when retention periods expire
- Legal hold capability to pause deletion during investigations or litigation
Policy driven retention ensures compliance video storage aligns with legal, regulatory, and business needs. It also helps control storage costs in a growing corporate video library.
End to end audit logs
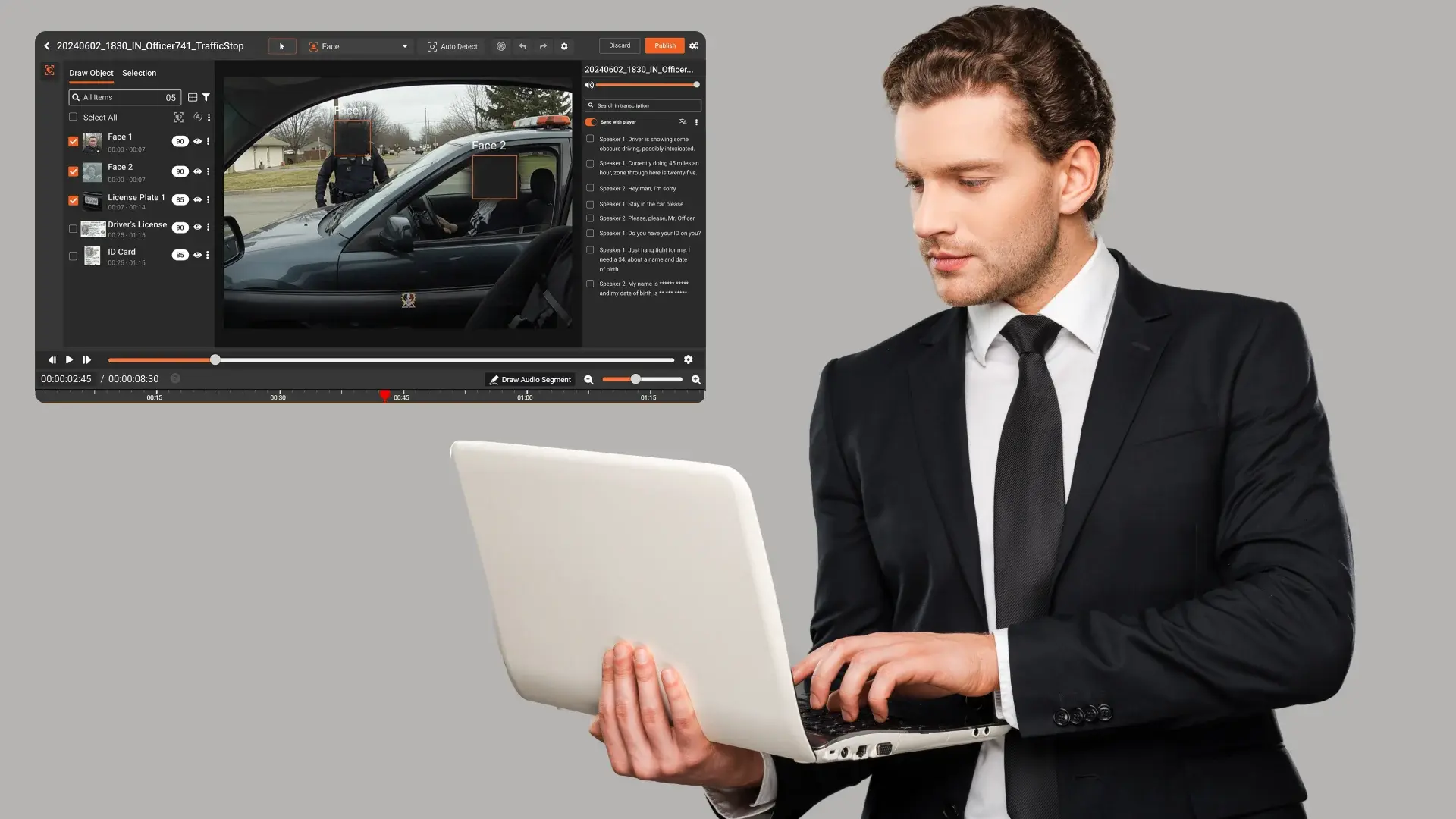
Comprehensive audit trails for video are central to governance. You need visibility into key activities, such as:
- Uploads, edits, deletions, and changes in permissions
- Views, downloads, embeds, and external shares
- Admin actions and configuration changes
These logs should be tamper resistant, exportable, and reportable. They support internal audits, data protection impact assessments, incident response, and regulator inquiries.
Compliance requirements for enterprise video governance
Video compliance is not a single framework. It is a combination of obligations that apply to your corporate video library. These typically include legal evidence, privacy rules, and industry regulations.
Legal evidence and chain of custody
Video often becomes evidence in disputes, claims, or investigations. Examples include:
- HR cases and workplace conduct reports
- Customer interactions and sales commitments
- Operational incidents and safety reviews
To stand as reliable evidence, your system must preserve integrity and chain of custody. That means:
- Original files stored securely with checksums or hash validation
- Time stamped audit logs of access and modifications
- Controlled exports with traceable recipients
Again, governance turns a corporate video library into a trusted system of record that legal and compliance teams can rely on.
Privacy and data protection obligations
Most corporate videos contain personal data. Faces, voices, names, screens, and sometimes sensitive information. A compliant video governance model should address:
- Lawful basis for recording and processing video
- Regional storage for data residency, when required
- Retention aligned with privacy principles of minimization and purpose limitation
- Controls to restrict cross border access when necessary
Advanced implementations may add redaction, consent workflows, or anonymization for specific uses. But even without automation, a corporate video library must support clear policies and technical controls that back privacy commitments.
Industry and regional regulations
Depending on your sector, your corporate video library can fall under additional rules, such as:
- Financial services communication retention and monitoring
- Healthcare privacy and security standards
- Public sector information governance, disclosure, and records acts
Secure video management in these environments requires close alignment between system capabilities and regulatory requirements. This includes encryption, access control, logging, and retention, all configured in line with written policy.
How governance drives trust and adoption for video at scale
Governance is not just about avoiding penalties. It also drives adoption. Employees and leaders will not fully use a corporate video library they do not trust.
When users believe that:
- Sensitive recordings are restricted by design
- Access is transparent and auditable
- Content will not suddenly disappear or leak
They are more willing to record real discussions, capture expert knowledge, and move key workflows into video. This is how the corporate video library shifts from scattered recordings to a central, governed knowledge base.
On the other side, compliance teams gain confidence when they see that video governance matches the standards already applied to email, chat, and documents. With clear policies and controls, they can support wider video adoption without adding unmanaged risk.
Governance features every corporate video library should require
To turn intent into practice, organizations need specific capabilities in their platform. A governed corporate video library should provide:
- Centralized role based access control integrated with existing identity systems
- Configurable video access control policies by group, role, and content type
- Comprehensive audit trails for video activities with search and export
- Policy based video retention policies, legal hold, and defensible deletion
- Encryption in transit and at rest, plus controlled external sharing
- Support for regional storage, data residency, and segregation where needed
- Administrative controls for approvals, publishing workflows, and review
Together, these capabilities define a secure video management environment that can scale. They also give compliance, legal, and security teams the levers they need to enforce enterprise video governance consistently.
How EnterpriseTube supports governed corporate video libraries
Many organizations choose EnterpriseTube to centralize video in a governed platform instead of scattered tools. This model treats the corporate video library as a first class system of record, not a simple content repository.
EnterpriseTube's approach to video governance typically includes:
- Central hub for all corporate video, integrated with conferencing and collaboration tools
- Fine grained permissions and identity aware video access control
- Global and channel level video retention policies aligned to record schedules
- Detailed audit trails for video, supporting compliance and investigations
- Configurable sharing options, from internal only to controlled external access
This structure turns a fragmented corporate video library into a single, governed environment. It allows security and compliance teams to set policies once, then apply them consistently everywhere video is created, stored, and accessed.
Most importantly, it shifts video from an unmanaged risk to a trusted source of evidence and institutional knowledge. That is where sustainable video adoption lives.
People also ask
How is a corporate video library different from general cloud storage
A corporate video library is purpose built for video content. It supports streaming, transcripts, thumbnails, and granular video access control, along with audit trails for video. General cloud storage focuses on files and lacks the governance depth, playback experience, and compliance features needed for regulated video.
Who should own governance for the corporate video library
Ownership is usually shared. IT or digital workplace teams run the platform. Compliance and legal define video governance policies, including video retention policies and sharing rules. Security oversees secure video management and access control. Together, they define a joint operating model.
What is the first step to improving video governance
Start with an inventory and risk assessment. Map where video lives today, who owns it, what types of content exist, and how it is currently shared. Then define a target state for your corporate video library with clear policies for access, retention, classification, and audit.
How long should we keep corporate videos
Retention varies by content type, industry, and jurisdiction. Training, HR, customer interactions, and operational videos may all have different schedules. Organizations typically align video retention policies with existing records management rules, then configure their corporate video library to enforce them automatically.
How do audit trails for video help in investigations
Audit trails show who accessed a video, when, and what they did. During investigations, this helps establish timeline, scope of disclosure, and potential impact. It also helps verify whether specific parties saw a video or whether content was shared outside intended audiences.
Can we safely share videos externally and still meet compliance requirements
Yes, if external sharing uses strong video access control. That includes authenticated access, time bound links, optional passwords, and restricted download. Audit trails for video should capture all external views and access events. This maintains control while enabling collaboration.
How does a governed corporate video library support privacy regulations
Governance supports privacy by enforcing limited access, region specific storage when needed, defined retention, and transparent logging. Combined, these controls reduce unnecessary exposure of personal data and support data subject requests, such as access or deletion, across video assets.
What metrics indicate that video governance is working
Leading indicators include reduced use of unmanaged channels for storing video, consistent use of the central corporate video library, fewer ad hoc access exceptions, faster response to legal and compliance requests, and improved audit outcomes related to video handling and storage.
Jump to
You May Also Like
These Related Stories

HIPAA-Compliant Video Redaction Tools for Healthcare

Managing Access in Enterprise Video Platforms: Why It Matters


No Comments Yet
Let us know what you think