Enterprise Video Platform that Understands Context, not Just Content
Find the exact moment, insight, or answer hidden in your meeting recordings, training sessions, organizational knowledge assets, virtual events, and online patient interactions using natural-language questions.
Our enterprise video platform ensures secure video content management and deployment across on-premises, private cloud, hybrid, and SaaS.
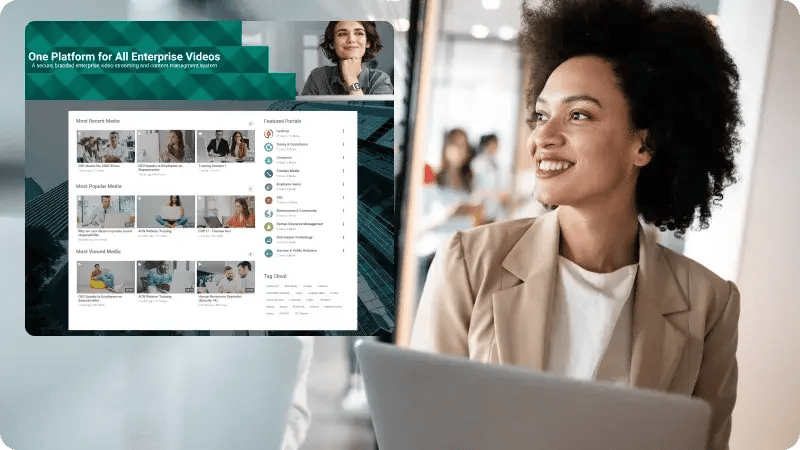
Enterprise Video Platform Trusted by Fortune 500 Companies and Government















Enterprise Video CMS Features for Streamlined Video Workflows
How Businesses Use Our AI-powered Enterprise Video Platform
Why VIDIZMO EnterpriseTube?
VIDIZMO EnterpriseTube is a Gartner-recognized enterprise video platform powered by artificial intelligence (AI). It offers advanced security, flexible deployment options, and granular video analytics to streamline enterprise video content management using a scalable AI video platform for business.
Enterprise Video Integration for Unifying Video Content Management














Flexible Deployment Options for Your Enterprise Video Platform
On-premises
Maintain complete control with an on-premises deployment, ideal for organizations with specific infrastructure requirements.
Cloud
Opt for enhanced security and control with a dedicated private cloud or choose Government Cloud for compliance with federal standards.
Hybrid
Combine the flexibility of cloud and on-premises solutions with hybrid deployment, offering the best of both worlds for versatile needs.
SaaS
Enjoy the benefits of cloud-based access, automatic updates, and scalability with our SaaS deployment model.
Manage Your Video Content Securely with the AI-powered Enterprise Video Platform
Top-of-mind Questions
An enterprise video is a form of content that is used by businesses to communicate with internal and external stakeholders, organize live events and webinars, increase brand awareness and outreach to a global audience, train and upskill employees, extract actionable insights from videos, and more.
Examples of enterprise video include corporate communications videos, patient consultation videos, training videos, marketing videos, live events and webinars, etc. Enterprise videos are used in multiple industries, including healthcare, financial services, insurance, law firms, energy and utilities, sports, and more.
An enterprise video platform is a specialized software designed to stream, manage, analyze, protect, and share enterprise video content, such as corporate communications videos, training videos, marketing videos, meeting recordings, live events, and more. Advanced enterprise video platforms manage the entire video content lifecycle from video content ingestion to data retention and sharing.
The key features of an enterprise video platform include the following:
- On-demand and live video hosting
- AI-powered video workflows
- White-label branding
- Adaptive bitrate streaming
- Enterprise-grade video content delivery network
- Centralized video library
- Granular video analytics
- Security, encryption, and access controls
- Flexible deployment, including on-premises, private cloud, hybrid, and SaaS
AI enhances video content management in enterprise settings in the following ways:
- AI-powered search for searching videos through spoken words, AI-generated tags, objects and text appearing in videos, and more
- Automatic generation of content tags for streamlined organization and retrieval of enterprise video content
- AI transcription and translation of video content in multiple languages for greater accessibility and wide audience reach
- Video summarization and chaptering for creating short summaries and breaking down long videos into easily consumable chapters
- AI-powered video analytics, including object detection and tracking, sentiment analysis, emotion detection, brand recognition, and more
Many industries, including healthcare, financial services, insurance, law firms, energy and utilities, and sports, largely benefit from enterprise video solutions in the following manner:
- Healthcare: Healthcare providers host patient consultation recordings, aftercare videos, and healthcare staff training content on a secure, HIPAA-compliant enterprise video platform to improve patient care.
- Financial Services: Financial services providers train their employees through engaging training videos covering the areas of fraud prevention, risk management, AML compliance, and more.
- Insurance: Insurance firms benefit from enterprise video solutions by training their Special Investigations Unit (SIU) team members, claim adjusters, appraisers, and sales agents regarding anti-fraud techniques, AML compliance, underwriting, claims management, and more.
- Law Firms: Law firms with global offices use enterprise video solutions to train their attorneys and ensure compliance with the Continuing Legal Education (CLE) program.
- Energy and Utilities: Energy and utilities companies ensure mission-critical video communications using enterprise video solutions.
- Sports: Sports organizations use enterprise video solutions to train their athletes and on-ground staff by using precision training backed by frame-by-frame analysis.
Enterprise video platforms ensure content security using features such as advanced at-rest and in-transit encryption, multifactor authentication (MFA), granular access controls, single-sign-on (SSO), secure embedding, IP and geo-restrictions, audit log, and other content security and protection features.

.webp?width=990&height=990&name=Corporate%20Communications%20(1).webp)



